Start Exploring Keyword Ideas
Use Serpstat to find the best keywords for your website
How to update the TLS protocol version on the website
What is the TLS protocol
This protocol is regularly improved and updated by IETF to ensure strong encryption, authentication, and data integrity. The latest version of the specification at the moment is TLS 1.3, which appeared in August 2018.
The need for an updated data protection protocol arose in 1999, as vulnerabilities were discovered in the SSL protocol. Now all versions of the SSL protocol have been successfully attacked using POODLE. The specified attack allows substituting user data and decrypting information transmitted by a secure data channel by byte.
What is the difference between the SSL and TLS protocols
TLS has some differences with the SSL protocol: the keys and the list of font sets differ, there is a difference in the pseudo-random PRF function and the HMAC hash function used to build a block of symmetric keys when encrypting data. A number of algorithms have been added to the TLS protocol to ensure the security of the data channel.
In fact, many users continue to call the TLS protocol "SSL encryption". This term has been widely adopted and is usually used by providers who actually offer TLS protection:

SSL vs TLS
TLS 1.0 vs. 1.2. How to install the most secure version of the protocol
Google experts found a fundamental flaw in the RC4 code used in TLS 1.0 and 1.1. Tests determined that these versions are not secure enough. The identified vulnerability is classified as CVE-2014-8730.
To ensure reliable data protection, modern protocols use 256-bit encryption keys, which are almost impossible to attack successfully.
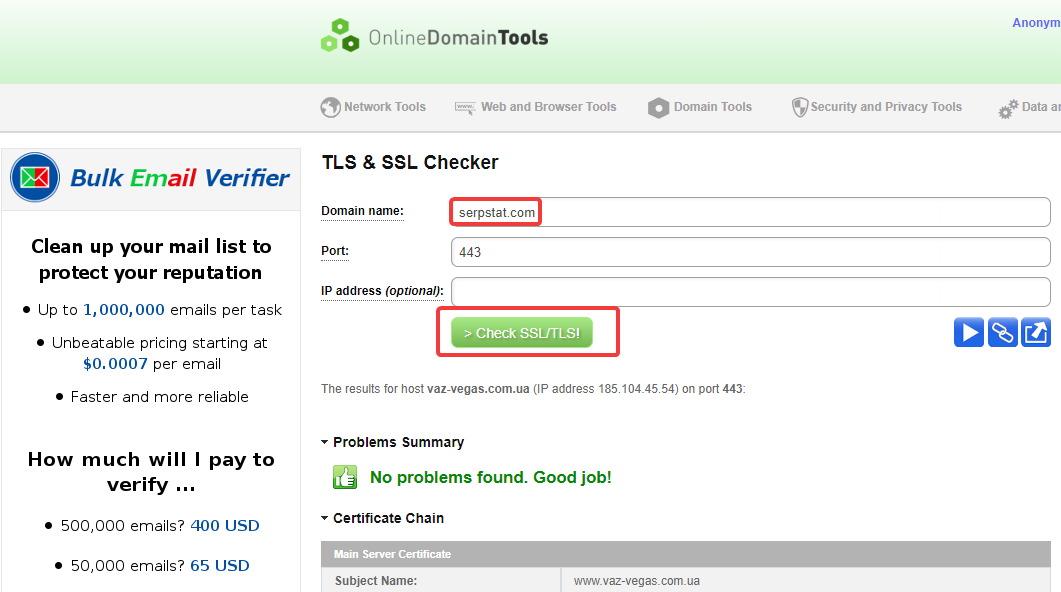
To check the current version of the protocol used on the website, you can use the SSL-checker service. This tool allows you to get a detailed report on the SSL and TLS versions used on the project.
To check, enter the domain address and click "Check SSL / TLS":
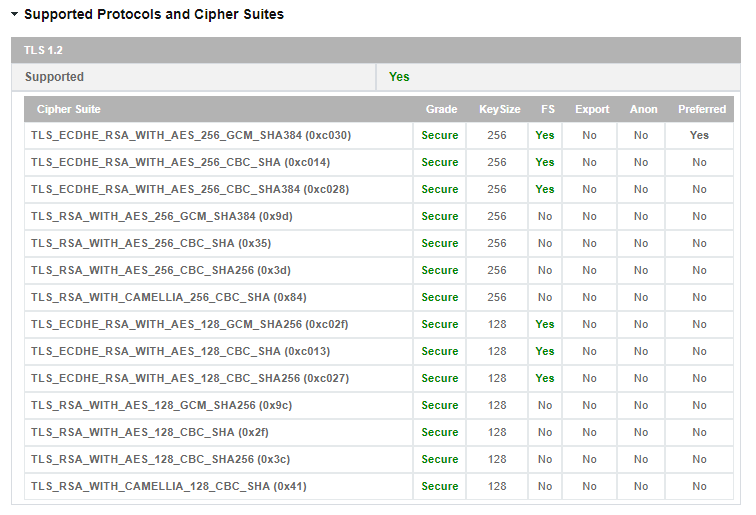
For example, to register an update of the TLS version on the Nginx server, you need to enable the SSL option on listening sockets, placing it in the server block. Additionally, you must specify the address of the files with the server certificate and secret key:
server {
listen 443 ssl;
server_name www.site.com;
ssl_certificate www.site.com.crt;
ssl_certificate_key www.certifikate-key.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
...
}Conclusion
At the moment, cryptographers consider versions of TLS 1.2 and higher to be safe and stable.
To install a secure version of the SSL certificate, you need to pay attention to its characteristics, as the TLS protocol must be at least version 1.2. The received certificate must be registered in the server settings with the required version of TLS.
 " title = "How to update the TLS protocol version on the website 16261788348048" />
" title = "How to update the TLS protocol version on the website 16261788348048" /> | Run Site Audit |
Speed up your search marketing growth with Serpstat!
Keyword and backlink opportunities, competitors' online strategy, daily rankings and SEO-related issues.
A pack of tools for reducing your time on SEO tasks.
Discover More SEO Tools
Tools for Keywords
Keywords Research Tools – uncover untapped potential in your niche
Serpstat Features
SERP SEO Tool – the ultimate solution for website optimization
Keyword Difficulty Tool
Stay ahead of the competition and dominate your niche with our keywords difficulty tool
Check Page for SEO
On-page SEO checker – identify technical issues, optimize and drive more traffic to your website
Recommended posts
Cases, life hacks, researches, and useful articles
Don’t you have time to follow the news? No worries! Our editor will choose articles that will definitely help you with your work. Join our cozy community :)
By clicking the button, you agree to our privacy policy.
