Start Exploring Keyword Ideas
Use Serpstat to find the best keywords for your website
Common Errors in Configuring SSL Certificate Chains and How to Fix Them


Regarding internet security, SSL certificates are the standard method to secure web-based communication. Using Secure Socket Layer certificates keeps data secure between websites and their users.
However, ensuring SSL certificates are configured correctly can be challenging to get just right and can leave websites vulnerable to attacks if not done correctly.
Let's dive in and explore the most common errors that can occur in SSL certificate chains and how to fix them. But first, what is SSL?
Quick Introduction to SSL
We're all familiar with SSL, even if we often overlook its prominence on every website we visit. And without getting too far into web protocols, the "S" part of HTTPS in your browser's URL bar stands for "secure," and that security is completed with SSL encryption.
SSL, or Secure Sockets Layer, is a protocol that encrypts data sent between a client (the browser, such as Chrome or Firefox) and a web server. Even though most people say "SSL" to refer to this secure transmission, SSL has been preceded by Transport Layer Security (TLS) – SSL and TLS are used interchangeably.
SSL/TLS protocols ensure the transmitted data's confidentiality, integrity, and authenticity. And it's this encryption method that ensures sensitive information, such as passwords and credit card numbers, cannot be intercepted during web traffic communication.
SSL, or Secure Sockets Layer, is a protocol that encrypts data sent between a client (the browser, such as Chrome or Firefox) and a web server. Even though most people say "SSL" to refer to this secure transmission, SSL has been preceded by Transport Layer Security (TLS) – SSL and TLS are used interchangeably.
SSL/TLS protocols ensure the transmitted data's confidentiality, integrity, and authenticity. And it's this encryption method that ensures sensitive information, such as passwords and credit card numbers, cannot be intercepted during web traffic communication.
Why is SSL Certificate Chains Important?
SSL certificate chains ensure that a trusted third party issues the SSL certificate a server presents. If not, a warning message will appear, indicating that the SSL certificate is untrusted and the connection is not secure.
Without SSL certificate chains, it's impossible to determine whether a website is entirely legitimate and trusted through the web communication process. SSL certificate chains ensure that data sent between the client and server is encrypted and secure and help prevent cybersecurity vulnerabilities.
It's important to note that SSL certificate chains are not infallible. While a somewhat sophisticated attack, a trusted CA may issue an SSL certificate to a malicious actor, allowing them to impersonate a legitimate website. This is a "man-in-the-middle" attack and can be difficult to detect.
Root Certificate Authority (Root CA)
At the top of the certificate chain (during communication) is the root certificate. Web browsers and operating systems come pre-installed with a list of trusted Root Certificate Authorities. Some of the trusted security leaders are DigiCert, Symantec, and Microsoft. Root certificates are the ultimate trust anchor in the SSL/TLS infrastructure.
Intermediate Certificate Authorities (Intermediate CAs)
Intermediate CAs are certificates issued by the Root CA. These certificates are used to create a chain of trust between the root certificate and the end-entity certificate. Intermediate CAs, also known as subordinate CAs, accompany the final issued certificate.
End-Entity Certificate
The end-entity certificate, also known as the server certificate, is the final certificate presented by the server to the client during the SSL/TLS handshake. This certificate binds the domain name(s) through the original Certificate Signing Request (CSR). The intermediate authority signs this certificate containing the server's public key.
While there are many ways to generate the CSR through your web hosting provider, it can also be done directly on the command line with this terminal command:
[code]openssl req -new -newkey rsa:2048 -nodes -keyout serpstat.key -out serpstat.csr[/code]
The contents of the generated CSR file will be used to submit to the Certificate Authority. And the "key" file is the private key, which must be kept secure – never submit the private key to any certificate authority.
This final certificate is verified by the web browser for its authenticity. Please note free solutions from Let's Encrypt are perfectly fine to use as well.
Common Errors in Configuring SSL Certificate Chains
SSL certificate chains provide an important layer of security, but misconfigurations can occur, leading to errors that compromise security. Here are some of the most common errors:
Incomplete Certificate Chain
An incomplete chain is the most common error when a server presents an SSL certificate without its complete certificate chain. In other words, the server fails to provide all the intermediate certificates that link the end-entity SSL certificate back to the trusted root certificate. This can result in a warning message or even a broken HTTPS connection. To avoid this error, ensure that your SSL certificate chain includes all the necessary intermediate certificates.
Mismatched Certificate Authority (CA) Bundle
Another common error is a mismatched certificate authority bundle. This happens when a server presents an SSL certificate with a CA bundle different from the issued CA bundle.
Put another way, the browser expects a specific set of intermediate certificates to be included in the SSL certificate chain, but the server provides a different set. This can also cause a warning message and a broken connection. To avoid this error, ensure your SSL certificate chain includes the correct set of intermediate certificates.
Expired or Revoked Certificates
Expired or revoked SSL certificates can cause errors since they're no longer valid. Ensure your SSL certificates are renewed before they expire, and any revoked certificates are replaced immediately. Failure to do so will cause a broken HTTPS connection and display a warning.
Incorrect Certificate Order
The order of SSL certificates in a certificate chain matters. The SSL certificate chain should be ordered properly in the final CRT file. Start with the issued SSL certificate at the top, followed by the intermediate bundle, and finally, the root certificate at the end. The order matters and is critical to avoid errors.
Self-Signed Certificates in the Chain
Using a self-signed SSL certificate instead of a trusted third-party CA can be acceptable, depending on the use case. However, self-signed certificates in an SSL chain can cause trust issues and warning messages. It's important to avoid using self-signed certificates in your certificate chain instead of certificates from a trusted third-party CA.
How to Identify SSL Certificate Chain Errors
Identifying SSL certificate chain errors will help to diagnose and troubleshoot potential security issues. And believe it or not, errors in configuring SSL certificates are actually quite common. These steps below will most likely uncover issues you didn't even know existed.
Using SSL Tools
SSL tools are helpful in identifying SSL certificate errors. These tools are excellent for scanning the server's SSL certificate and providing detailed information about any errors detected.
The best tool is the SSL Server Test by Qualys SSL Labs. This tool checks the SSL configuration of a server and provides a detailed report on any issues found.
This tool provides a grade based on the security of the SSL certificate chain, and it will also alert you to potential vulnerabilities that might need further addressing.
Also, while not part of this article's scope, reviewing best practices on SSL configuration for your web server flavor is critical, which can be done with Mozilla's SSL tool.
Analyzing Server Logs
Monitoring server logs can help identify many technical errors, including SSL issues. Server logs contain information on all requests made to the server. Tracking error messages can help determine the cause of the error and help resolve it.
Analyzing server logs is the best method to uncover technical issues, and doing so can also be used to identify unauthorized access attempts, even SEO-related issues. The information uncovered can be used to identify potential security threats and take appropriate action.
Perform SEO audit
To ensure the effective functioning of a website, it is necessary to check not only the SSL certificate but also a number of other technical parameters. When it comes to identifying these issues, Serpstat can be incredibly useful. The platform provides SEO solutions for conducting a full website analysis, as well as improving security, traffic, and conversions.
To check your website, go to Serpstat and create a project with the chosen domain.
Then go to the Site audit. Select the project you created earlier and change the settings if necessary.
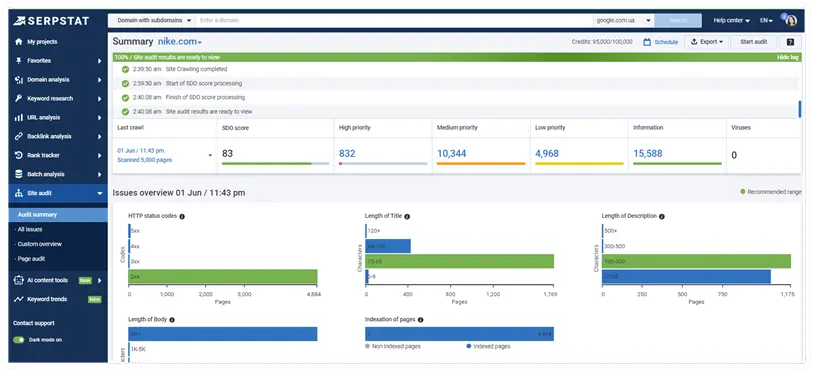
After processing the data, Serpstat will provide you with detailed information about all the issues with your website. If there are any problems with the SSL certificate, you will be able to see them among issues.
Unlock Your Website's Hidden Potential
Identify and resolve hidden issues affecting your online presence with Serpstat's Site Audit tool.
Browser Error Messages
Browser error messages can also provide insights into SSL certificate errors. Common browser error messages include "This site can't provide a secure connection" and "Your connection is not private." And you can always click on the padlock in the URL/address bar and check for issues and certificate validity there.
Fixing SSL Certificate Chain Errors
SSL certificate chain errors can be frustrating and confusing, but fortunately, they can often be fixed with simple steps.
Completing the Certificate Chain
If a website/server presents an incomplete certificate chain, it's crucial to identify the missing intermediate certificates and install them correctly to complete the chain. This can be done by contacting the certificate authority (CA) that issued the SSL certificate and requesting the missing intermediate certificates. Once you have the missing certificates, you can install them on your server in the order mentioned above.
The correct certificate order is as follows:
Renewing Expired Certificates
When an SSL certificate expires, simply renew the certificate before it expires to avoid errors. This can also be done by contacting the CA that issued the SSL certificate and requesting a renewal. It's worth noting that some CAs may offer automatic renewal services, such as Let's Encrypt, which can help ensure that SSL certificates are always up-to-date.
Replacing Self-Signed Certificates
The best practice is to use SSL certificates issued by trusted third-party CAs. However, using self-signed certificates for testing purposes, intranets, and internal-only facing websites, servers, and applications is also common. Replacing self-signed SSL certificates with trusted ones can help avoid trust issues and warning messages.
Always ensure that any self-signed certificates are replaced with trusted ones before deploying a website or application to a production environment.
Conclusion
When users encounter an SSL certificate error, they should not proceed to the website, as their information is at risk. Instead, they should contact the website administrator to resolve the issue. Ignoring SSL certificate errors can compromise the security of transmitted data.
SSL certificate chains are essential in securing online communications between servers and clients. Understanding and identifying common SSL certificate chain errors and how to fix them is crucial in ensuring secure online communication.
Speed up your search marketing growth with Serpstat!
Keyword and backlink opportunities, competitors' online strategy, daily rankings and SEO-related issues.
A pack of tools for reducing your time on SEO tasks.
Discover More SEO Tools
Backlink Cheсker
Backlinks checking for any site. Increase the power of your backlink profile
API for SEO
Search big data and get results using SEO API
Competitor Website Analytics
Complete analysis of competitors' websites for SEO and PPC
Keyword Rank Checker
Google Keyword Rankings Checker - gain valuable insights into your website's search engine rankings
Recommended posts
Cases, life hacks, researches, and useful articles
Don’t you have time to follow the news? No worries! Our editor will choose articles that will definitely help you with your work. Join our cozy community :)
By clicking the button, you agree to our privacy policy.